Sample Vendor Risk Management Policy / Derisking Ai Risk Management In Ai Development Mckinsey : The vendor is responsible for notifying all persons whose sensitive data may have been compromised as a result of the breach as required by law.
Sample Vendor Risk Management Policy / Derisking Ai Risk Management In Ai Development Mckinsey : The vendor is responsible for notifying all persons whose sensitive data may have been compromised as a result of the breach as required by law.. • banks should review their vendor risk management policies and processes to ensure that the bank is able to exercise sufficient oversight in each stage of risk management life cycle • banks may need to update risk management policies or reassess risk management policies depending on the level of risk and complexity of relationship A vendor risk management policy is vital to mitigating cyber risks across an organization's network ecosystem. Risk management controls against internal policies governance • report upon effectiveness of the program Vendor risk management (vrm) is the process of ensuring that the. Vendor risk management (vrm) is the process of managing risks associated with third party vendors.
Vendors and third parties can pose many risks including financial, reputational, compliance, legal, and more. You're only as strong as your weakest vendor. Due to stringent regulations regarding outsourcing, many institutions are. Legal issues, past performance, and creditworthiness are some of the common vrm issues that all companies review frequently. A vendor risk assessment checklist is a tool used by procurement officers to assure vendor compliance with regulatory requirements such as data privacy, due diligence, and security risks.

The policy applies to all activities and processes associated with the.
Setting appropriate limits and controls on third party vendors helps reduce the risk of security incidents, financial liability, loss of community trust, and embarrassment. It's important to understand these risks, what they are, and how argo can readily identify any issues, concerns, or constraints pertaining to these risks. The aim of risk management is to maximise opportunities in all organisation activities and to minimise adversity. (hsx) will manage security risks that are introduced by third parties, including contracted vendor service providers. Learn why gartner named archer a 2020 leader for it vendor risk management tools. • banks should review their vendor risk management policies and processes to ensure that the bank is able to exercise sufficient oversight in each stage of risk management life cycle • banks may need to update risk management policies or reassess risk management policies depending on the level of risk and complexity of relationship Risk management controls against internal policies governance • report upon effectiveness of the program With the right team, a strong strategy, and a solid vendor management policy, you can reduce risk. 1.2 defining your policies and procedures for monitoring third parties. Risk is the likelihood is the likelihood that a harmful risk owner is the person(s) responsible for. Vendor risk management (vrm) is the process of ensuring that the. The policy is one of three documents. Vendor management policies are a foundational element of your vendor management program.
Vendor management process in a company must conform with the following vital steps in order to be as effective and thorough as possible. The policy identifies who's responsible for vendor management as well as acknowledges regulations, identifies elements of managing vendors, broadly outlines concepts of due diligence, risk assessments, contract management and more and determines how you keep the senior management team and board informed. This is often a multidisciplinary effort that covers a variety of vendor related risks.the following are illustrative examples of vendor risk management. • banks should review their vendor risk management policies and processes to ensure that the bank is able to exercise sufficient oversight in each stage of risk management life cycle • banks may need to update risk management policies or reassess risk management policies depending on the level of risk and complexity of relationship The policy applies to all activities and processes associated with the.
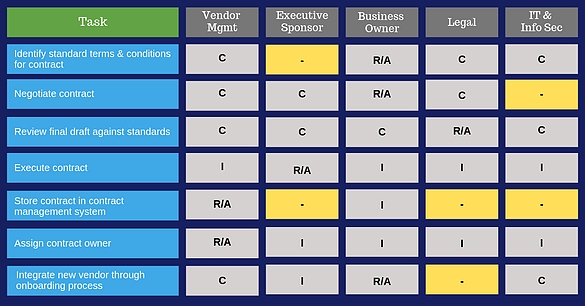
Due to stringent regulations regarding outsourcing, many institutions are.
You can tailor these subtasks to fit the needs of your organization. This includes so much more than service levels, management process and contract management. Enterprise & operational risk management. Legal issues, past performance, and creditworthiness are some of the common vrm issues that all companies review frequently. The aim of risk management is to maximise opportunities in all organisation activities and to minimise adversity. This vendor risk due diligence plan template provides a sample of steps to take in a due diligence process. To help manage the risks posed by vendors, here are seven considerations: Vendor risk management (vrm) is a broad category that encompasses all measures that your organization can take to prevent data breaches and ensure business continuity. The vendor representative will be permitted access only to individuals with whom they have an appointment. Setting appropriate limits and controls on third party vendors helps reduce the risk of security incidents, financial liability, loss of community trust, and embarrassment. Purpose and scope this policy establishes the process for the management of risks faced by organisation. Vendor management consist the identification, qualification, re qualification, management of the auditor shall verify whether proper policies/procedures/process controls exist and are followed to annual risk assessment (vendor management) : At the time of arrival at the specific hospital facility, the vendor representative will be required to visit the vendor management system kiosk and obtain a vendor badge.
A vendor risk assessment checklist is a tool used by procurement officers to assure vendor compliance with regulatory requirements such as data privacy, due diligence, and security risks. Vendor risk management (vrm) is a broad category that encompasses all measures that your organization can take to prevent data breaches and ensure business continuity. The policy identifies who's responsible for vendor management as well as acknowledges regulations, identifies elements of managing vendors, broadly outlines concepts of due diligence, risk assessments, contract management and more and determines how you keep the senior management team and board informed. Vendor management process in a company must conform with the following vital steps in order to be as effective and thorough as possible. • technical expertise to review a vendor's controls and document in business terms the risk, and recommendation to address the vendor's control deficiencies • train/educate internal business sponsors on vrm policy, expectations, and risk management best practices and promote risk awareness opportunit.

Vendor management process in a company must conform with the following vital steps in order to be as effective and thorough as possible.
Developing a clear risk strategy and mitigation plan. With the right team, a strong strategy, and a solid vendor management policy, you can reduce risk. Vendor management process in a company must conform with the following vital steps in order to be as effective and thorough as possible. Due to stringent regulations regarding outsourcing, many institutions are. Purpose and scope this policy establishes the process for the management of risks faced by organisation. Vendor management consist the identification, qualification, re qualification, management of the auditor shall verify whether proper policies/procedures/process controls exist and are followed to annual risk assessment (vendor management) : • banks should review their vendor risk management policies and processes to ensure that the bank is able to exercise sufficient oversight in each stage of risk management life cycle • banks may need to update risk management policies or reassess risk management policies depending on the level of risk and complexity of relationship This is often a multidisciplinary effort that covers a variety of vendor related risks.the following are illustrative examples of vendor risk management. At the time of arrival at the specific hospital facility, the vendor representative will be required to visit the vendor management system kiosk and obtain a vendor badge. Management and oversight policy compliance A vendor risk management policy is vital to mitigating cyber risks across an organization's network ecosystem. Vendor risk management (vrm) is a broad category that encompasses all measures that your organization can take to prevent data breaches and ensure business continuity. A practical guide to vendor management.
Komentar
Posting Komentar